Introduction:
In an era where cyber threats loom large and the traditional network perimeter has all but dissolved, enterprises require a more robust, adaptive approach to security. Zero Trust Network Access (ZTNA) provides such a solution, embodying the principle that nothing inside or outside the network should be trusted without verification. This blog explores the transformative power of ZTNA solutions and their pivotal role in fortifying enterprise security infrastructures.
Zero Trust Network Access: Enforcing a ‘Never Trust, Always Verify’ Security Model
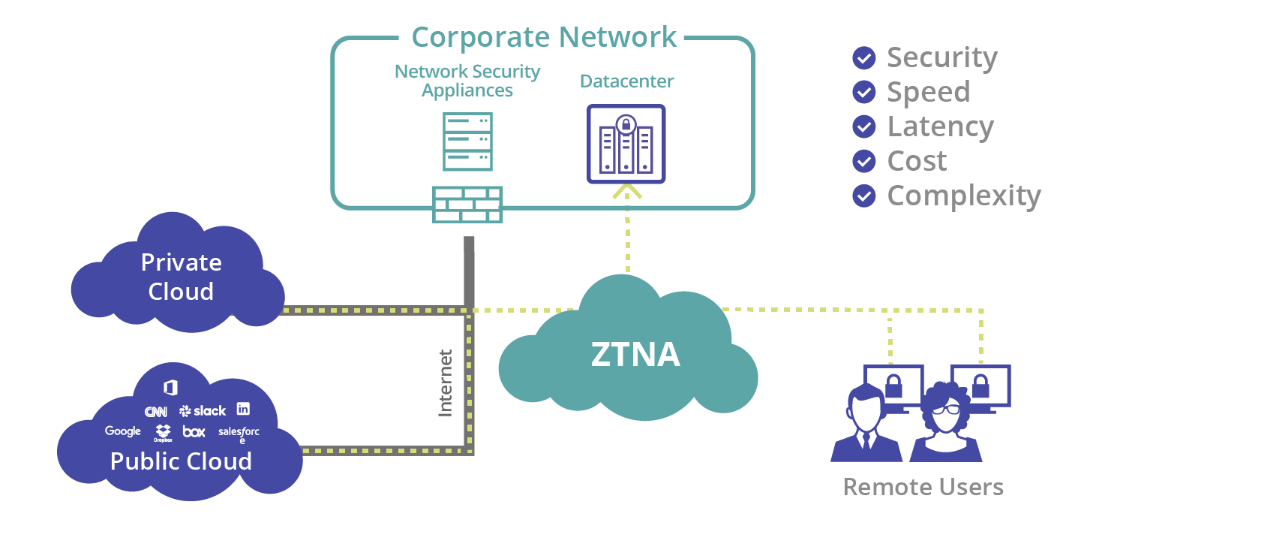
Zero Trust Network Access (ZTNA) is a security model and set of technologies that enforce strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are sitting within or outside of the network perimeter. ZTNA is built on the premise of “never trust, always verify,” which is a shift from the traditional “trust but verify” framework.
Key Features of ZTNA Solutions
- Identity-Based Access Control: ZTNA systems grant access based on the identity and context of the user and device, ensuring that only authenticated and authorized entities can access network resources.
- Microsegmentation: By segmenting the network into smaller, secure zones, ZTNA minimizes the lateral movement of threats within networks, enhancing security for sensitive data and systems.
- Least Privilege Access: Access rights are tightly controlled and limited to what is needed for users to perform their tasks, reducing the risk of insider threats and data breaches.
- Continuous Monitoring and Adaptation: ZTNA solutions continuously monitor network activities and adapt permissions dynamically, responding to new threats and changes in user status or behavior.
The Importance of ZTNA for Modern Enterprises
As businesses continue to embrace remote work, cloud services, and mobile computing, the need for traditional VPN solutions diminishes in favor of more secure, flexible access solutions. ZTNA provides:
- Enhanced Security Posture: By verifying all entities before granting access, ZTNA reduces the attack surface and mitigates the risk of data breaches.
- Support for a Distributed Workforce: ZTNA facilitates secure remote access by ensuring that security policies are consistently enforced, regardless of the user’s location.
- Scalability and Flexibility: With cloud-based deployments, ZTNA solutions can scale quickly to accommodate growing numbers of users and devices across geographic locations.
- Regulatory Compliance: ZTNA helps organizations meet stringent data protection and privacy standards, crucial for industries facing heavy regulation.
Choosing Wisely: Key Considerations for Selecting Your ZTNA Service Provider
Selecting an effective ZTNA solution involves several considerations:
- Comprehensive Security Features: Look for solutions that integrate seamlessly with existing security tools and offer end-to-end encryption, malware protection, and advanced threat detection.
- User Experience: Ensure the ZTNA solution provides a smooth, seamless user experience without compromising security.
- Vendor Reputation and Support: Choose providers known for their expertise in network security and robust customer support.
- Deployment Flexibility: Consider whether on-premises, cloud, or hybrid deployments best fit your organizational needs.
Embrace the Future of Security: Why ZTNA is Essential in Today’s Cyber Landscape
Zero Trust Network Access is more than a security solution; it’s a strategic approach that aligns with modern cybersecurity challenges and business practices. Implementing ZTNA can significantly enhance your organization’s security framework, support compliance efforts, and provide secure access in a perimeter-less world. As cyber threats continue to evolve, embracing ZTNA is not just wise—it’s essential.